Continuation of Privacy, Surveillance, Control (1): An Introduction.

At the heart of this discussion lies a simple truth: government is a necessary evil. This is a maxim that I believe is worth remembering, all the way down to a homeowners association.
Why government is necessary is fairly obvious; it is impossible to imagine a sophisticated society without centralized leadership to enforce rules fairly, maintain the peace, and provide services that would be infeasible at the individual level.
Why it is evil is less apparent; power corrupts.
The following chart shows the instances of political killings from 1946 to 2022. For this data, a targeted mass killing refers to the deliberate killing of at least 25 noncombatant civilians within a country during a given year, carried out by organized armed forces or groups, intended to destroy or intimidate a specific political, ethnic, or religious group.
The data does not quite capture the magnitude of the damage wrought. Depending on the definition, the sum of the targeted mass killings within a domestic population ranges from 100 million to 262 million over the past century. To put that in perspective, the estimates for the total sum of war casualties in this period ranges from 108 million to 150 million.
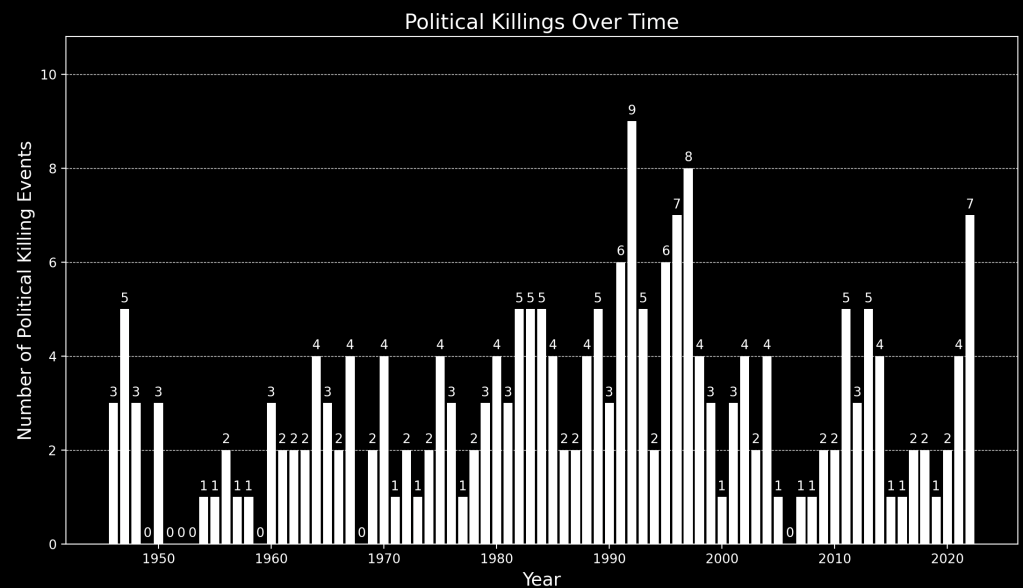
Admittedly, many of these killings take place in totalitarian regimes, and very few occur in democracies. However, recall that the Nazi party became the largest party in the Reichstag (German Parliament) in the July 1932 election. Hitler’s rise to power from that point was a series of legal and political maneuvers that culminated in dictatorship. Democracy is not immune to tyranny.
As R.J. Rommel, a political scientist who has done extensive research on democide, put it:
“The closer to absolute power, the more a regime’s disposition to murder one’s subjects or foreigners multiplies. As far as this work is concerned, it is empirically true that Power kills, absolute Power kills absolutely. “
This philosophical foundation was critical to the creation of the United States, born under the tyranny of the British monarchy. The American Constitution, the oldest still in use, is among the greatest pieces of writing in history. It has proven itself excellent because of its adaptability, acknowledgment of unalienable human rights, and its underlying skepticism of government.
The Fourth and Fourteenth Amendments are particularly important to the topic of this article.
“The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated…”
”…nor shall any State deprive any person of life, liberty, or property, without due process of law.”
In 2013 Edward Snowden exposed the NSA surveillance of Americans through the PRISM program. My naive initial reaction was to assume it was simply too much data to store or process. This was not the case then and it is certainly not the case now. Like many, I initially saw Edward Snowden as a traitor. I had animosity for him.
As I grew older, my opinion changed. I now see Snowden as a hero who acted in the interest of the American people, as a patriot ultimately should. His so-called treason was not against his country, but against a subsection of the government— unelected officials abusing illegal powers.
I separately support the mission of the NSA and the broader American intelligence community in their efforts to keep American citizen’s safe and prosperous. However, inherent to any modern intelligence agency is the ability to do indiscriminate and unchecked harm.
“I don’t want to see this country ever go across the bridge. I know the capacity that is there to make tyranny total in America, and we must see to it that this agency and all agencies that possess this technology operate within the law and under proper supervision, so that we never cross over that abyss.”
— Church Committee Hearings, 1975
Intelligence agencies are, in the scheme of political history, extremely young. Though intelligence—such as the deployment of spies—has been critical in military history for thousands of years, the expansion of surveillance abilities has gone parabolic in lockstep with technological growth since World War II.
The brutal history of the Nazi Gestapo and the Soviet NKVD may hardly need mention. The Gestapo was utilized to suppress opposition, round up Jews, and enforce Nazi ideology through torture, extrajudicial killings, and concentration camp deportations. The NKVD was likely more destructive, with an estimated 750,000 people executed in just two years of the Great Purge (1936-1938), many of them shot in the back of the head in NKVD basements. They maintained files on every soviet citizen, deeply scrutinizing them for anti-Soviet activities —often erroneously.
The East German Stasi (1950-1990) is considered to have enacted the greatest surveillance state in history. Roughly 1 in 6 East Germans was either full-time employees of the Stasi or informants. At their peak they maintained 1 billion pages of records on East Germans, including interactions, letters, and conversations. They effectively implemented Zersetzung, which directly translates to decomposition or decay in English, as a form of psychological warfare — blackmail, gaslighting, and social sabotage— designed to destroy a person, slowly and often imperceptibly, by leveraging intelligence against them.
It could be argued that these regimes were inherently repressive and destructive. However, the key point is that their evil was facilitated by an intelligence apparatus that was turned against a domestic population with no means to defend itself.
Fast forward to the post-Cold war era, where we see the development of electronic surveillance. This is such a monumental shift that it is arguably a difference in kind, not in degree. While intercepting letters, wiretapping, and espionage existed previously, mass surveilling, algorithmic and predictive decision making, and nearly ubiquitous access to our electronic lives is a paradigm shift. What the internet was to the global economy, it is too to the surveillance state.
Though similar issues are pervasive across the world, I will now focus only on America.
After 9/11 the United States became weaponized against the ambiguous threat of terror. There was justifiable fear in the country, which created the conditions for the rushed and under scrutinized Patriot Act to pass through the House (357-66) and the Senate (98-1).
- Section 215 allowed the government to collect phone records of millions of Americans without individualized suspicion.
- It broadened the Foreign Intelligence Surveillance Act (FISA) making it easier to obtain secret surveillance warrants on individuals suspected of terrorism.
- Section 505 granted the FBI authority to demand records from businesses without court approval, preventing them from informing the target.
- Section 802 broadened what qualifies as domestic terrorism.
The potential abuses of such laws, and the creeping expansion of power they enable, should be apparent after the historical review above.
The programs uncovered by Edward Snowden in 2013 had operated unobstructed from 2007 to 2015.
- PRISM program allowed the NSA to collect user data directly from major U.S. tech companies such as Google, Facebook, Apple, and Microsoft. The data included emails, chats, photos, videos, and stored files.
If the paranoia surrounding TikTok’s ascendence in America confused you, this should be enough context to understand why. Given China’s extensive surveillance state, I would posit that it is very likely that TikTok operates as a surveillance tool of the Chinese Communist Party.
- The NSA was collecting records of all phone calls made within the United States, including phone numbers, call durations, time stamps, and routing information.
- XKEYSCORE, described as the NSA’s most powerful surveillance tool, allowed analysts to search emails, browsing history, online chats, and social media activity. This program had famously little oversight, with NSA analysts able to search for individuals without prior approval.
- Cryptocurrency transactions were monitored and de-anonymized. Even applications such as Angry Birds, or Google Maps, were used to monitor location data and personal information.
- Journalists, activists, lawyers, and even world leaders such as Germany’s Angela Merkel was monitored and surveilled. Merkel’s response to the Obama administration for monitoring her personal phone was blunt:, “Spying on friends is not acceptable”. I agree.
In 2015, in the wake of the fallout from Snowden’s leaks, the USA FREEDOM ACT was passed, officially reigning in many of these programs. Automatic bulk data collection was stopped, replaced with a corporate partnership, where data could still be accessed with specific government requests.
However, corporate surveillance is just as insidious. Cloaked behind convenience and user experience, it operates without the checks and balances, however flawed, that constrain government.
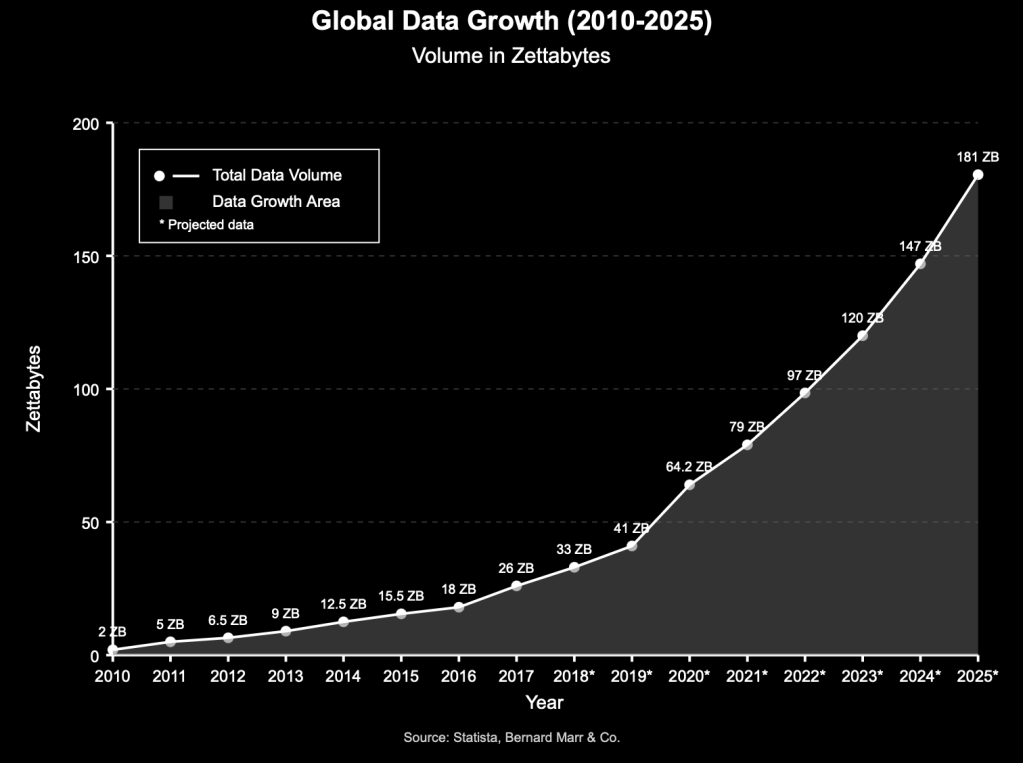
Personal data is being mined like a raw material, and the supply is growing exponentially. User behavior data is critical to modern tech companies, beyond what is necessary to provide the product or service. As described in Shoshana Zuboff’s book The Age of Surveillance Capitalism, you are not their customer, but instead their product. The real customers are businesses, advertisers, and governments buying access to predictive data.
It’s worse than that though. The predictive capabilities allow surveillance capitalists to not only predict behavior but to shape and modify it. Your social media algorithm does not only show you what you like— it tells you what to like.
As it stands now, society is at a worryingly vulnerable position to the power of these technology companies. Personal data is extracted through opaque, non-consensual, and often impossible-to-opt-out-of processes.
This power has already been wielded to influence democratic elections, such as when Cambridge Analytica harvested data from millions of Facebook users to build psychological profiles and micro-target them with political ads aimed at manipulating their voting behavior.
These are companies seeking to maximize profits, not societal welfare.
This asymmetry between the tech companies and the public will only increase across time unless there is sufficient pushback from the public. The utilization of technology cannot be avoided; it is part of modern life, not something one can reasonably opt out of. Being subject to surveillance and manipulation for using technology should not become acceptable.
Again, as stated in the previous post, resistance begins with awareness. Yet even among those who are aware of the extent of surveillance, there is often apathy. Some believe naively that they are immune to manipulation; others argue that they have nothing to hide. Neither are reasonable positions on the matter.
“Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.” – Edward Snowden
Society will slowly wake up to this reality—perhaps only after the implicit dangers are fully experienced. It will create a demand for privacy as a commodity, a response to the growing technological asymmetry favoring today’s surveillance capitalists. Much later, the democratic process may implement better legal safeguards to protect citizens and their proprietary data.
The choice we face is not only between privacy and surveillance, but also between autonomy and control. If we value freedom, we must always defend it—not just from governments, but from corporations that have quietly inherited the power of surveillance once reserved for states. Government is a necessary evil, and in today’s world, digital technology is too. Both must be treated with cautious respect, with full awareness of the power they possess and the corruption that is inherent in them.
Surveillance is control. Privacy is freedom.
